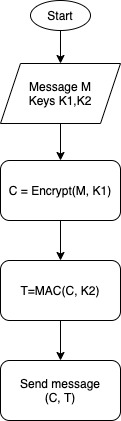
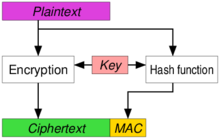
Architecture of the security module implementing the Encrypt-then-MAC... | Download Scientific Diagram

Architecture of the security module implementing the Encrypt-then-MAC... | Download Scientific Diagram
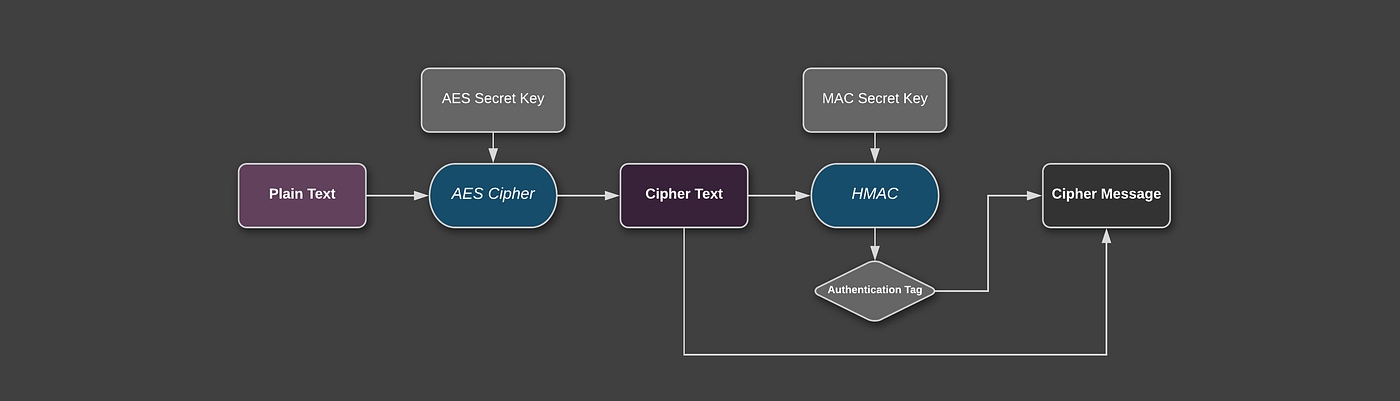
Security Best Practices: Symmetric Encryption with AES in Java and Android: Part 2: AES-CBC + HMAC | by Patrick Favre-Bulle | ProAndroidDev
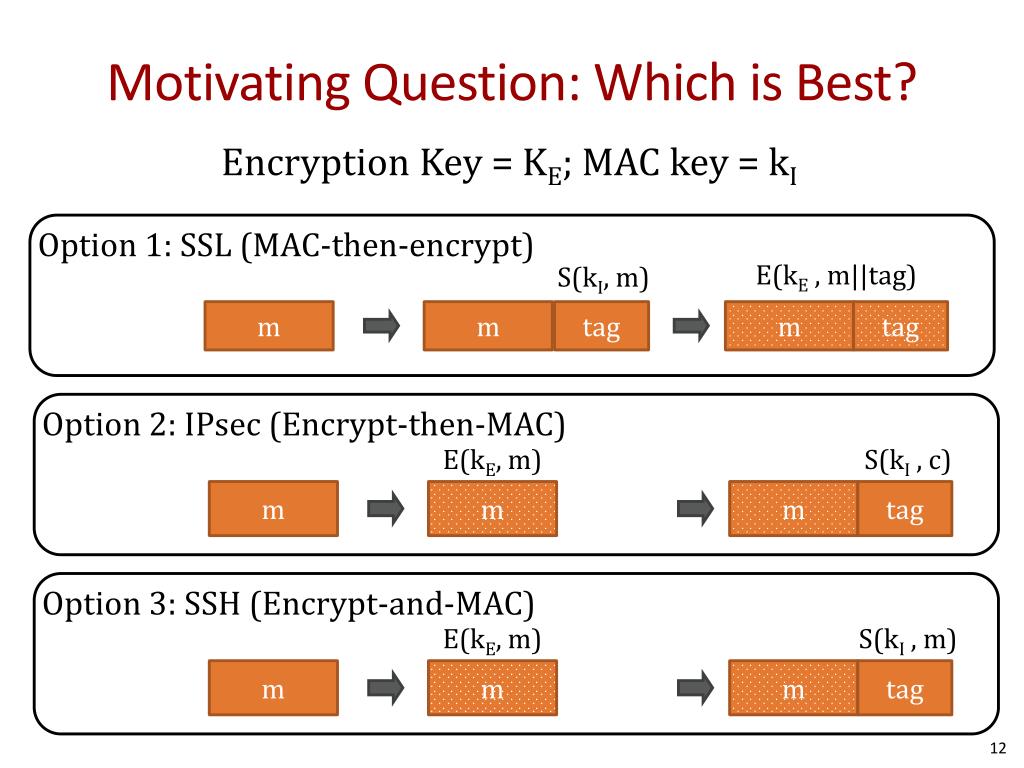
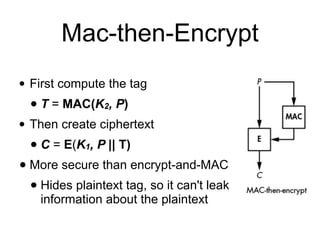
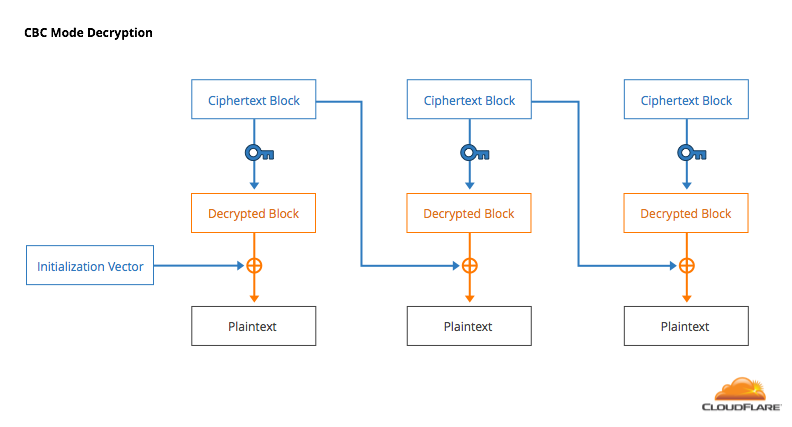
PPT - Authenticated Encryption and Cryptographic Network Protocols PowerPoint Presentation - ID:2850015
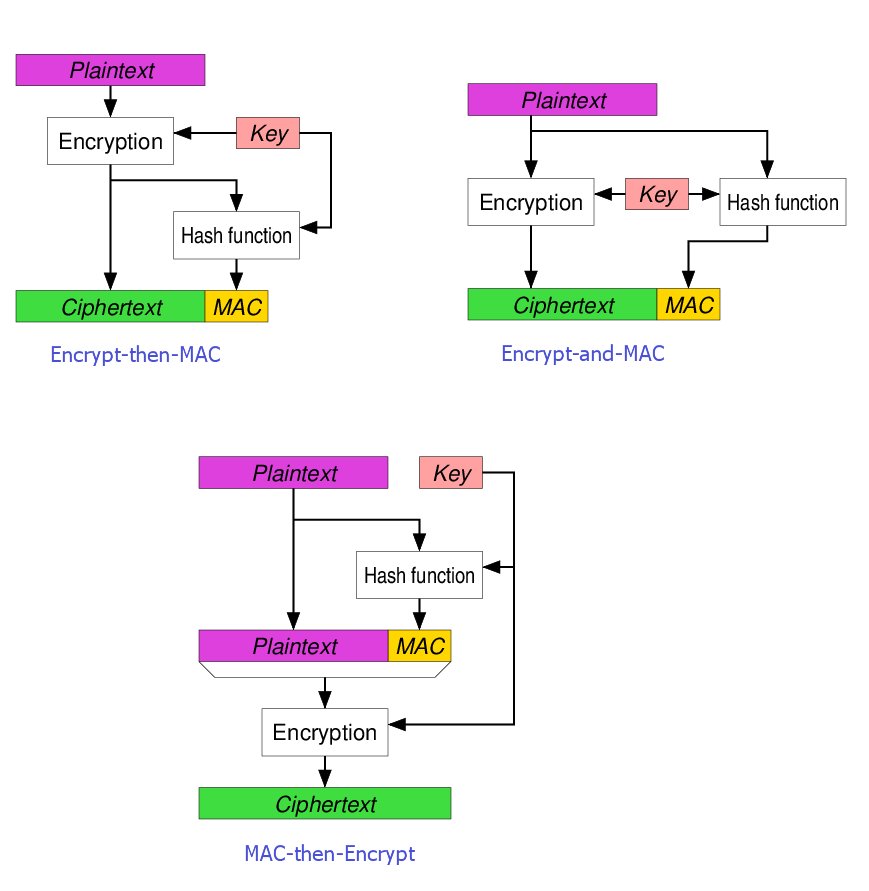
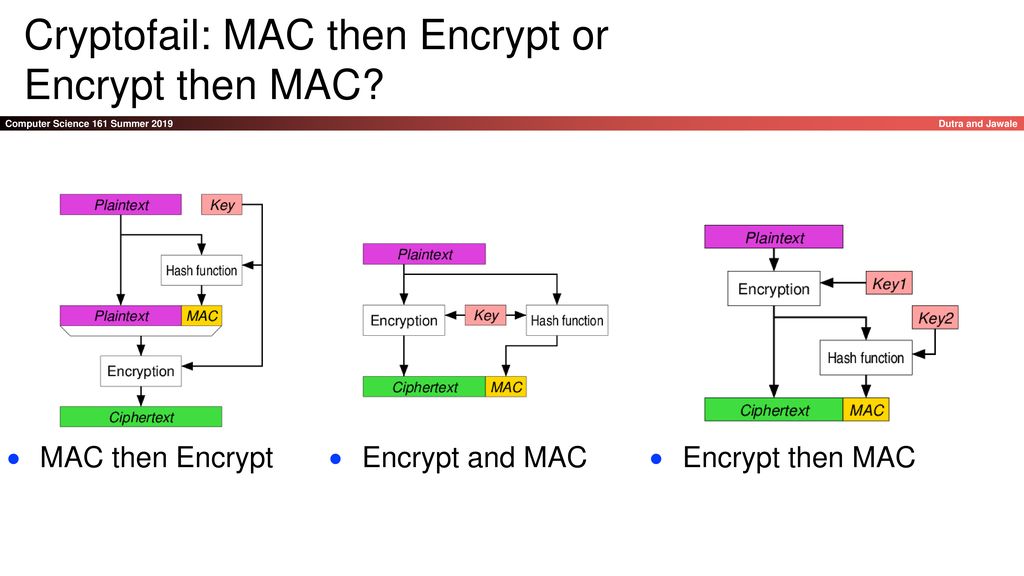
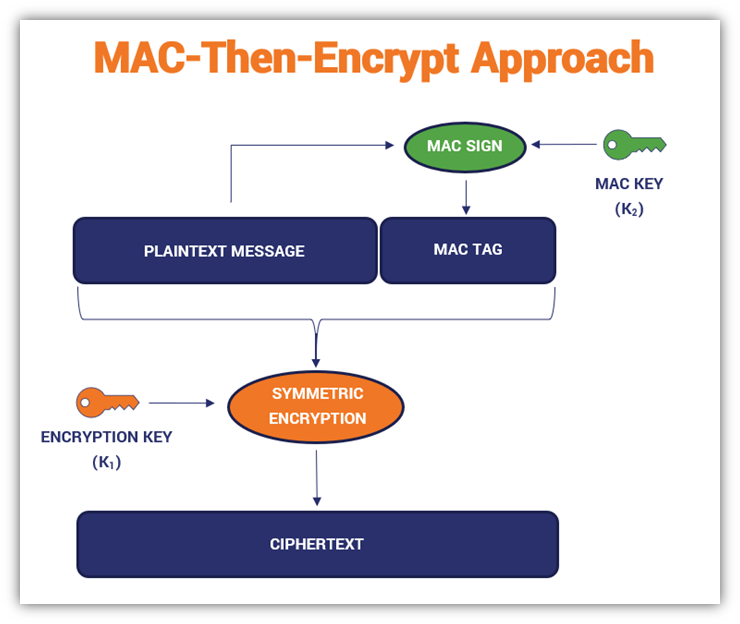
GK Palem on Twitter: "Among the three methods for #Blockchain #Ciphers the Encrypt-Then-MAC has been regarded as the highest definition of security with "strongly unforgeable" MAC, compared with MAC-then-encrypt or Encrypt -and-MAC. Authenticated
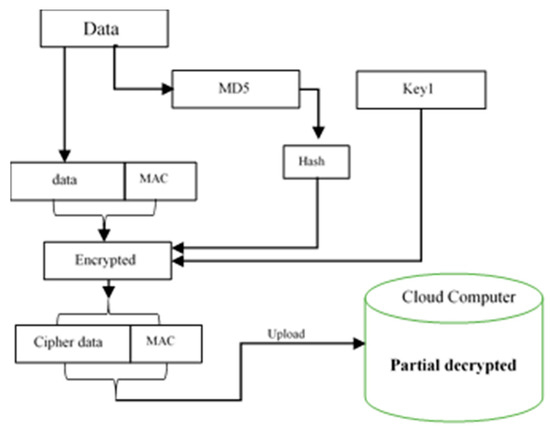
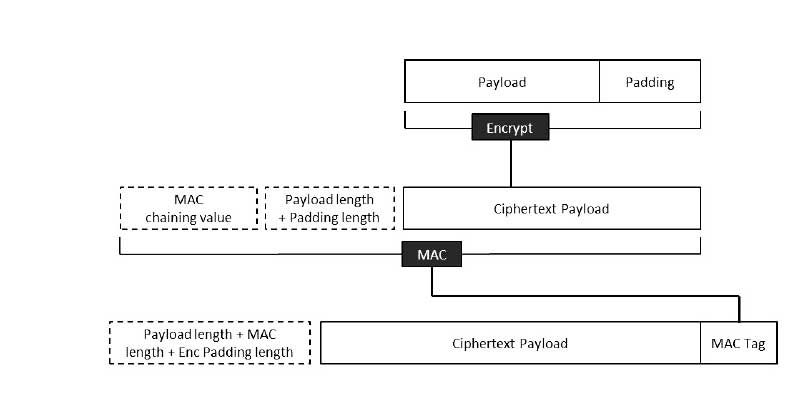
Electronics | Free Full-Text | Dual Authentication-Based Encryption with a Delegation System to Protect Medical Data in Cloud Computing